Core Impact is a centralized penetration testing tool from Core Security that enables security teams to conduct advanced, multi-phased penetration tests that can exploit numerous vectors, including network, client-side, and web applications.
Key Features
Certified Exploits
Utilize the exclusive and extensive exploit library, which is updated in real time and features commercial-grade exploits written and validated by experts.
Guided Automation
Automate routine and repetitive tasks with Rapid Penetration Tests (RPTs), which enable testers to focus on more complex exercises.
Integrations
Import data from popular scanners to easily validate vulnerabilities. Integrate with other pen testing tools like Metasploit, PowerShell Empire, and Plextrac to centralize testing and extend capabilities.
Patented Agents
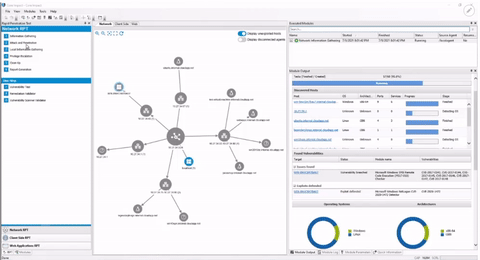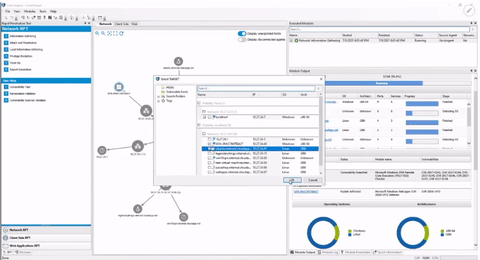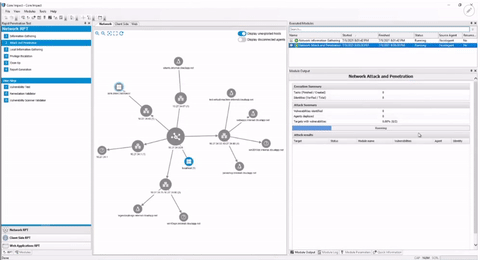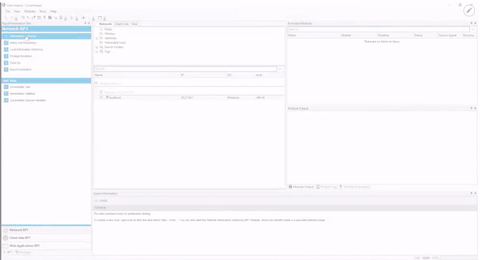
Inject agents into a targeted or compromised remote host and use encrypted communication to execute multiple tasks including information gathering, crawling a web application, or escalating privileges.
Automated Retesting and Remediation Validation
Retest remediation measures and verify that security patches or other compensating controls have been applied and have corrected security vulnerabilities.
Visibility
Determine the next steps of the testing process with the Attack Map, an interactive display of attack chains, pivoting, and other activities.
Centralized Reporting
Generate clear, thorough reports that can be used for remediation planning and proof of compliance.
Interoperability with Cobalt Strike
Layering offensive security solutions helps create a powerful proactive portfolio that keeps you ahead of attackers. While Core Impact is ideal for pen testing, Cobalt Strike is a bench red teaming tool with a focus on post-exploitation exercises, simulating a quiet long-term embedded threat actor in an IT network.
Users of both Core Impact and Cobalt Strike can take advantage of session passing and tunneling between the solutions. This interoperability extends the capabilities of both tools and can make engagements more efficient. For example, use a privilege escalation exploit to gain access to a network, and then spawn a Cobalt Strike Beacon to begin post-exploitation exercises.
Additionally, both tools can share resources. Any of Core Impact’s library of certified exploits can be launched directly through Beacon. Core Impact fully supports the Cobalt Strike BOF API, allowing Core Impact users to also be able to benefit from Community Kit extensions. Cobalt Strike can be purchased at a reduced price with any one of Core Impact’s pricing plans.
Featured Product Bundles and Suites
Core Impact can be bundled with different cybersecurity tools at a discounted cost to create a proactive portfolio that enables your organization to better anticipate attacks and push back against threats.
See all the bundles and suites to learn more and find out which is the best fit for your environment.
Core Impact Pricing
Core Impact’s tiered model provides the versatility needed to allow organizations to build their pen testing program at a reasonable pace and price.
Basic
Build the foundations of your pen testing program and start exploiting security weaknesses within your infrastructure. Features include network testing, rapid pen tests, reporting, and more.
Pro
Enhance your engagements and extend your reach without adding complexity. Features include network testing, rapid pen tests, test modules, client side testing, reporting, and more.
Enterprise
Rapidly mature your security and easily conduct penetration tests across vectors. Features include network testing, rapid pen tests, test modules, client side testing, web application testing, reporting, and more.
Head to the pricing page to learn more about these different pricing plans, any of which can take advantage of a discounted bundle with Cobalt Strike.