What is Red Teaming in Healthcare?
AIM
In healthcare red teaming, ethical hackers (cybersecurity experts hired by the healthcare organization) attempt to infiltrate the organization’s network and discover weaknesses that would result in compromise if not remediated. Red teaming utilizes any and all methods of attack available to threat actors, including social engineering, advanced persistent threats (APTs), phishing, baiting, pretexting, malware, and even physical reconnaissance and compromise.
Impact
Red teaming and adversary simulation allow highly targeted healthcare providers to run “fire drills” of a real-world attack. Last year, over 700 healthcare security incidents were reported to the US Department

of Health and Human Services Office for Civil Rights (HHS OCR), with roughly 186 million people affected. More regular red teaming in healthcare could bring down these numbers by showing healthcare data security teams where adversaries could successfully strike and warning them with enough time to fix it.
Challenges Specific to Healthcare
The healthcare industry has always been a hot target for attackers. First, the amount of sensitive health information, also known as protected health information (PHI), stored within healthcare organizations is surpassed only by the amount of personally identifiable information (PII) stored along with it. Attackers targeting healthcare providers have a good chance of stealing both. However, PHI is more valuable on the black market, as the Center for Internet Security (CISA) notes, making it an even more lucrative part of the pie. According to the Infosec Institute, on underground criminal forums, PHI garners the highest price on the black market, above any other data, including credit card data and PII.
Top Cyber Threats in Healthcare
We know threat actors are after sensitive healthcare information, but how are they obtaining it? The HHS OCR reported that hacking and ransomware experienced exponential growth in recent years:
- Hacking | 239% increase (2019-2023)
- Ransomware | 278% increase (2019-2023)
The healthcare industry, like any other, faces a barrage of threats from without and within. Some, like attacks on third parties, reflect trends across sectors but hit healthcare especially hard. Others come with the territory. In recent years, specific threats to cybersecurity in healthcare have come to include:
There are countless opportunities for cybercriminals to take advantage of any weakness in the healthcare chain. When threat actors steal patient data, they can sell it for hundreds of times the going rate of non-medical information because of the numerous and lucrative things that can be done with it. PHI - like diagnoses, medications, and insurance details - has a longer “shelf life” than things like credit card numbers that can easily be changed or expire. This allows threat actors to exploit it for a longer amount of time. Additionally, PHI can be used to illicitly obtain medication, file fake medical claims, and more.
Evaluate Your Safeguards for Patient Data
How would your infrastructure hold up against an attacker? Put your defenses to the test with Cobalt Strike.
Healthcare Cyberattack Statistics
How likely is an entity within the healthcare sector to experience a cyberattack? Very likely. A recent study indicated that 92% of all healthcare organizations were the victim of at least one cyberattack in the past year alone (up 4% from last year’s already high 88%). Average price tags of healthcare breaches were also high, averaging $9.77 million per incident for the industry in 2024.
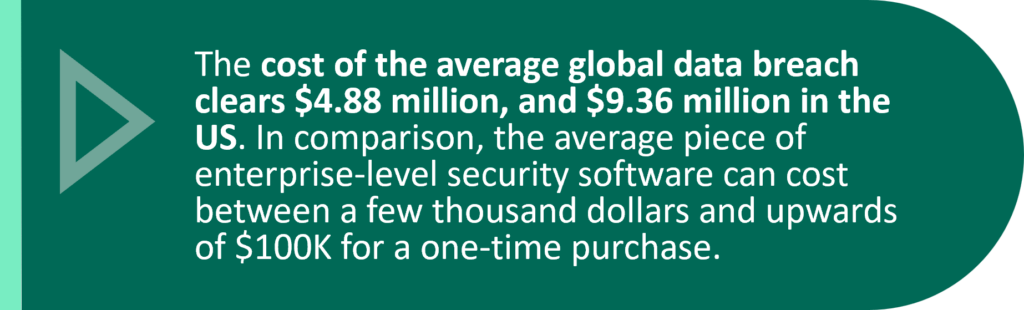
Individual costs
The Path Forward
The Tools
Key Terms to Remember
Be prepared with Cobalt Strike.
Red teaming can uniquely prepare healthcare organizations by leveraging all methods of attack available to threat actors; from spear phishing executives to pretexting, BEC scams, phishing campaigns, AI-generated voice calls, hidden ransomware links, and more. However, healthcare red teaming requires proper tools.
Fortra’s Cobalt Strike, a sophisticated threat emulation tool, can be utilized by security teams of any maturity level to perform their own red team engagements and adversary simulations. It not only tests internal defenses but informs blue teams of security issues, so they are better prepared.