Western Regional CCDC was pretty epic. Given the level of interest in red activity, I’d like to share what I can. So much happened, I couldn’t keep up with all of it. That said, here’s my attempt to document some of the red team fun from my perspective at Western Regional CCDC.
* . . . . o o o o o * _____ o _______ * ____==== ]OO|_n_n__][. |lamer| * [________]_|__|________)< |ville| * oo oo 'oo OOOO-| oo\\_ ~~~|~~~ * +--+--+--+--+--+--+--+--+--+--+--+--+--+
The scenario was interesting. Students were put in charge of a Computer Crime Defense Center. Part of their job involved protecting a repository of computer viruses.
Blue teams were given a 2-hour head start to secure their systems and change passwords. I was a little worried about this, but this worry was unfounded. The WRCCDC Black Team is far more evil than any red team I have ever seen. Students had to cope with a very strange network which included things like kill yelling at them for not saying the magic word, gratuitous appearances of ASCIIQuarium, and systems named in very confusing ways. Imagine my surprise when a UNIX box I quickly backdoored called home as winxp. Yeah…
https://t.co/pzJ9inDo1B https://t.co/8Mgagk6Miz #wrccdc More black team fun…
— James Schneider (@disturbedmime) March 30, 2013
The Low Hanging Fruit
Once the waiting period was over, we sat down at our systems and prepared to “facilitate” a learning experience. The first hint that we started was Vyrus’s music blasting through the convention center.
They say Apple is evil. #macbook #wrccdc #redteam pic.twitter.com/wm2jwXq2Th
— WRCCDC (@wrccdc) March 29, 2013
It took us a few minutes to get going. Apparently ICMP was not passing through from our space to the teams. So we had to resort to finding systems by looking for open services. I started with a quick sweep for port 22 and 445 with the Metasploit Framework’s ssh_version and smb_version modules. I focused on one team space at a time, to allow myself to learn the layout of the competition environment without waiting forever.
It didn’t take long to discover a few Windows 2003 systems. Even after a 2-hour delay, these were pretty easy to sweep with ms08_067_netapi. Stopping access to port 445 with a host-based firewall would have easily defeated this.
Once I had access to a few Windows systems, Windows Credential Editor helped me get ahold of the default password: Opensolaris1. A few of us discovered and pasted this credential to IRC at about the same time.
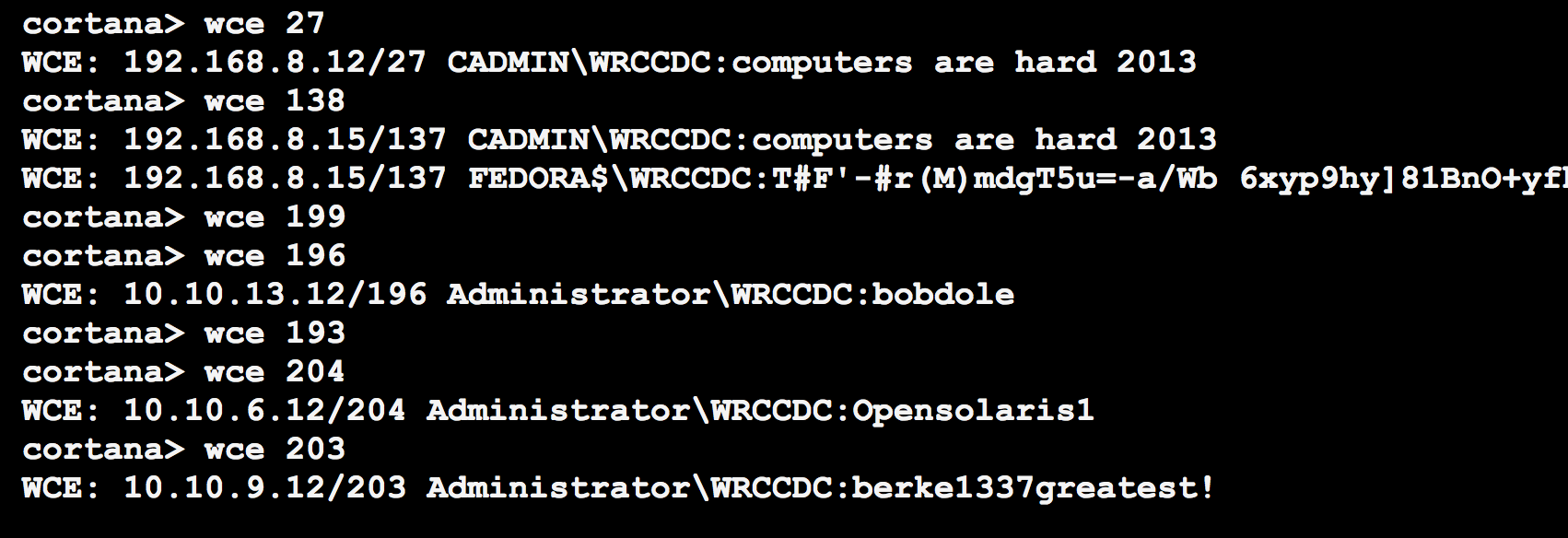
I had a Cortana script ready to persist like crazy on the Windows systems. I’m not giving away my full kit for this year, yet… but it’s spiritually similar to last year’s kit. I also made a special effort to drop files to disk that anti-virus does not catch at this time.
I was able to verify that persistence worked by viewing the Beacons on the three Cobalt Strike team servers I had up. Cobalt Strike’s Beacon is an asynchronous post-exploitation agent. It doesn’t maintain a persistent connection to me, rather it periodically calls home to request the tasks that it should run.
Once I had default credentials, my next step was to attempt to login to all UNIX systems over SSH and to sweep all other Windows systems (with port 445 open) with psexec.
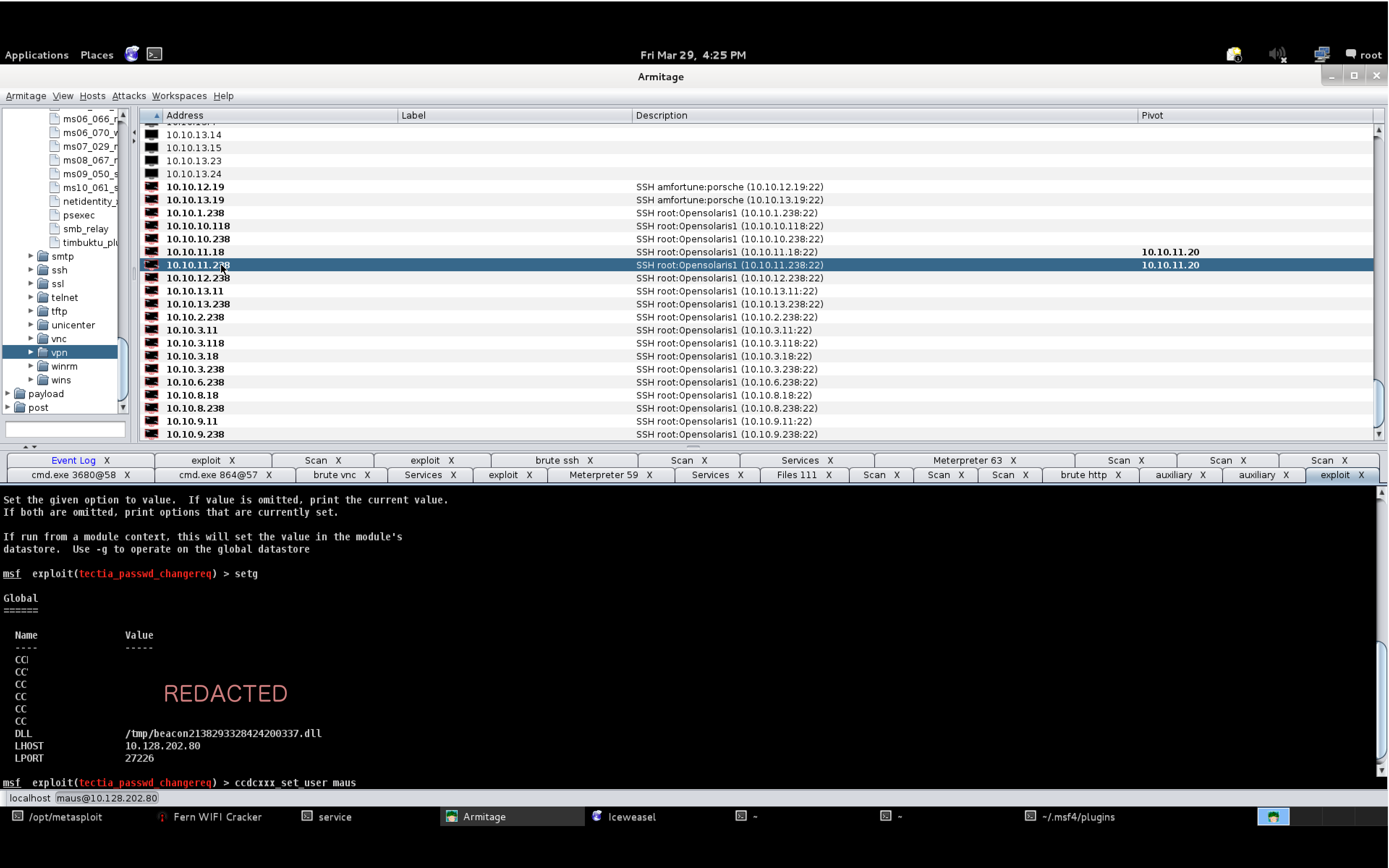
Even 2-hours in, the default credentials bore a lot of fruit. They allowed us to lay down some persistence on the UNIX systems and to capture a Windows 2012 server system from one team.
Taking Points
The red team is able to affect blue team scores in three ways. Gaining access to a host takes away points. Stealing certain data flags takes away points. We’re also able to disrupt services or deface websites, which takes away points because the teams will fail service checks.
Ahh Rick Astley, you're never gonna give me up. #wrccdc pic.twitter.com/YYb7NalviO
— uosןᴚɐɔ ןǝɐɥɔıɯ (@blainecarlson) March 30, 2013
Managing Persistence
I spent most of my time during the competition managing Beacons across multiple servers. I would task Beacons to spawn sessions to one of the team servers my red team compatriots were connected to. The idea is this, if a blue team member sees notepad.exe connecting to an IP address, they may squash that connection and block that IP address, but so long as they don’t discover the Beacons, they can’t keep us out.
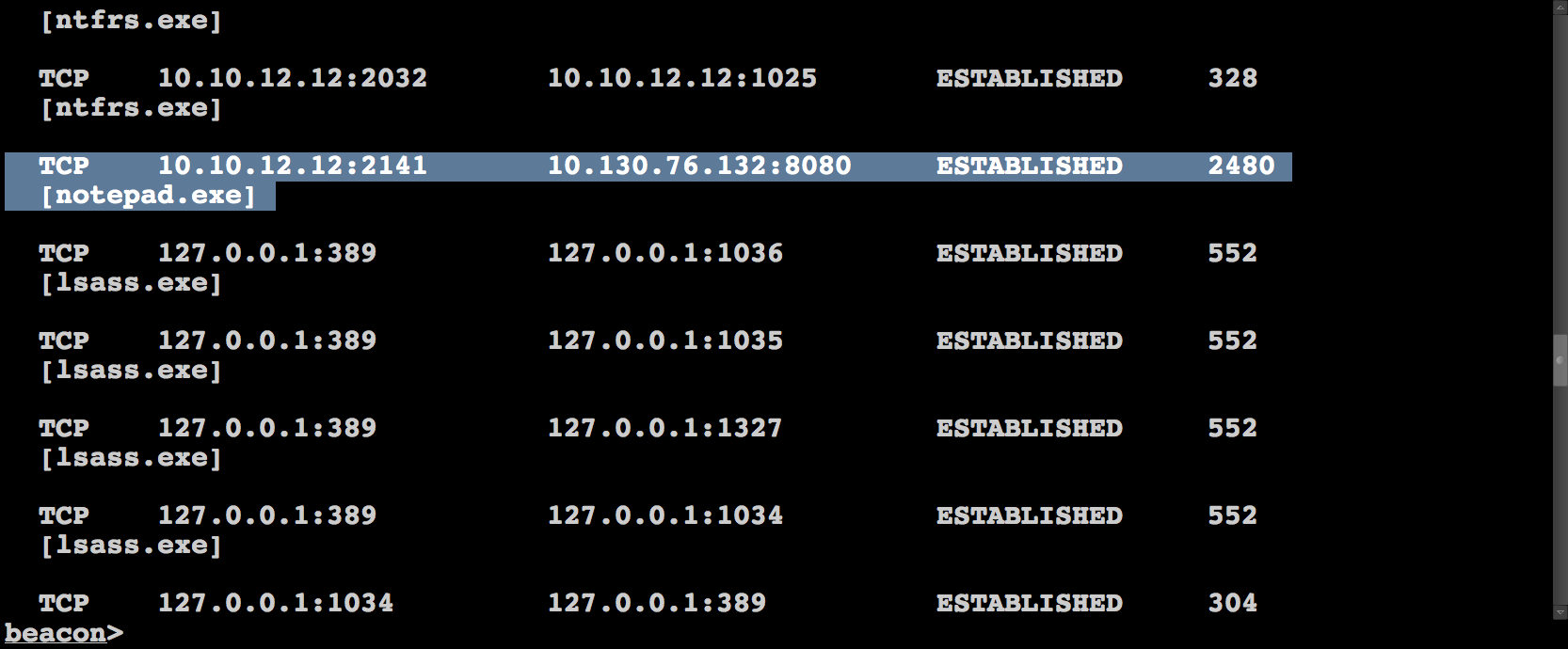
Sometimes, we’d get access to a Windows system that we did not have before. This may be because the team’s system or network was down during our earlier exploiting frenzy. When this happened, I’d help whoever gained access to the system pass it to me, so I could install persistence on it. This system would now be available for anyone connected to the team server to abuse or pivot through.
Sometimes, I’d fight to protect our persistence:
Later in the event, the two lead teams had creative egress filtering and routing in place. I spent my time trying to understand, through trial and error, what they would and wouldn’t allow. Eventually, I ended up having to task Beacon to send reverse https sessions to a team server located in Amazon’s EC2. This gave the folks interested in dealing with these teams the opportunity to do so.
Special Attention
Friday, before dinner, I opted to give each team special attention. My goal was to loop through each team, one at a time, understand their networks, understand what changed, and find the low hanging fruit I could grab and persist on again. I didn’t want to miss easy access opportunities from being too busy.
I started with team 13 and tasked any beacons I had calling home to give me a session. Once I had my sessions, I ran Windows Credential Editor again to get any plaintext passwords. I also dumped password hashes and gave them a quick pass through John the Ripper.
I then setup a pivot through a Windows system, discovered live hosts with an ARP scan, and used several Metasploit Framework modules to discover the open services.
If I didn’t have access to a Windows host for a team, I would try to work from a Linux system. Conveniently, the competition black team had a Raspberry Pi device installed on each team’s network. It was taped under a table and connected directly to their switch. These devices had default credentials and NMap. In several cases, I was able to use the Raspberry Pi to run NMap against a team and import the results into Cobalt Strike.
In the few cases that we didn’t have access to any systems (one team adopted a strategy of staying down the entire event!), I would run NMap from a non-team server system and import the results into Cobalt Strike.
Once I understood which services the team had open, I would then attempt all known credentials against their Windows and UNIX hosts. If a Windows 2003 system was not hooked, I would use the trusty ms08_067_netapi exploit again. I should state–ms08_067_netapi is the only memory corruption exploit I used during this event.
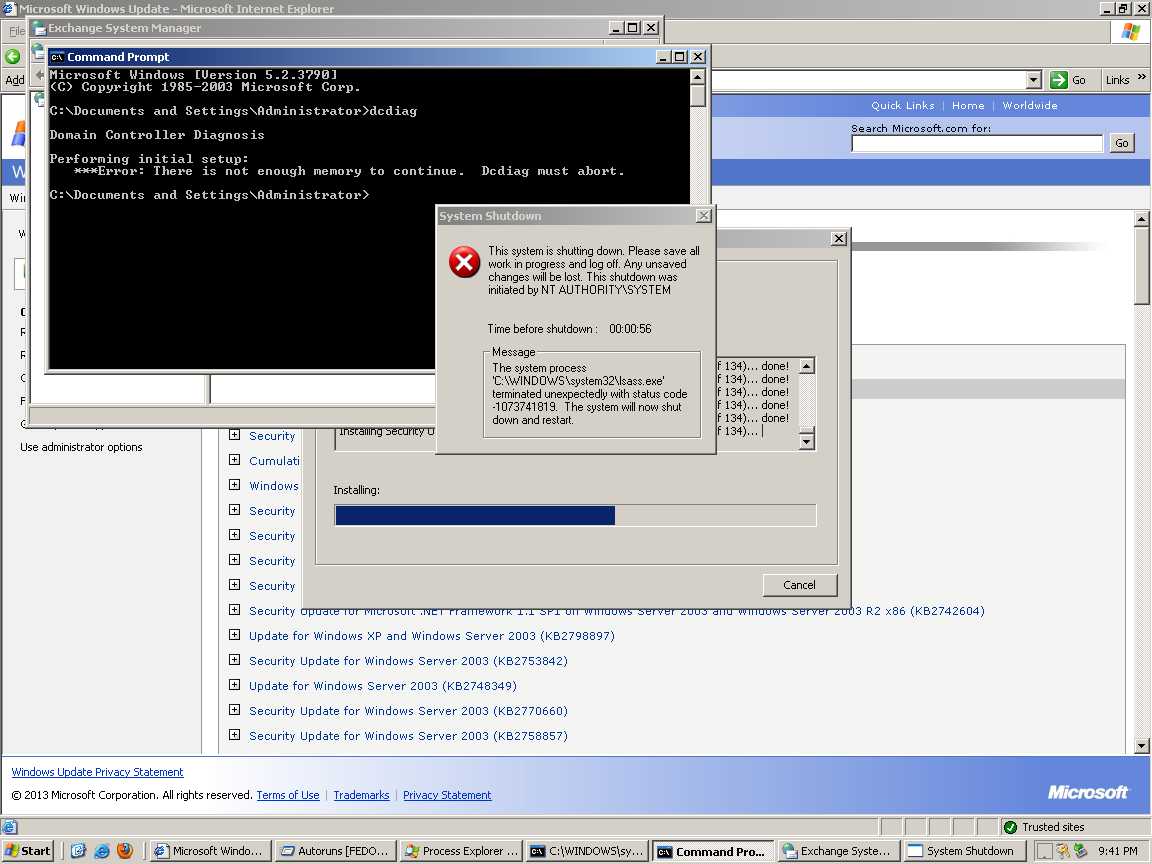
During this step of the game, I got lucky as several blue teams opted to use the same password on different systems. This reused password allowed me to get access to and persist on their Windows 2012 systems.
Checking a few choice file locations yielded access to other assets as well:
Shenanigans
The Western Regional CCDC Red Team had some crazy scary talent. Alex Levinson spent a lot of time administering forums for the blue teams. Alex, Vyrus, and Maus also built a system to track our accesses, credentials, and report our activity to the competition judges. This was a big help and we were able to pilot some ways to have the Metasploit Framework feed data to this system, automagically.
Our #wrccdc red team including @armitagehacker @theKos @michaelmcg19 @jrozner @vyrus001 @alexlevinson pic.twitter.com/fU8OUIJwMu
— WRCCDC (@wrccdc) March 31, 2013
Kos took over the X desktop for two teams and gave them full screen VNC access to each other.
https://twitter.com/theKos/status/317842914178920448
I also heard of minecraft servers getting setup on blue team systems. An important way to provide red team with a break.
Is that another minecraft servers I see running on #blueteam servers at #wrccdc? pic.twitter.com/F2CINfnrJX
— uosןᴚɐɔ ןǝɐɥɔıɯ (@blainecarlson) March 30, 2013
I spent some time poisoning hosts entries on student systems to prevent them from getting to their inject scoring engine site, google, and others.
A lot of pretty funny pranks came from the red team. I wish I was able to keep up with all of it and detail it to you here. Despite this shortcoming, I hope this perspective helped shed some light on the red team activity that took place over the weekend.
#wrccdc top three teams, thanks for another great year pic.twitter.com/QEvOHFzWT4
— Patrick O'Connor (@dontrebootme) March 31, 2013
Congratulations to our 2013 #WRCCDC Winners! 3rd: CSU: San Bernardino, 2nd: UC Berkeley, and 1st: Cal-Poly Pomona http://t.co/nKnRQ5dVEc
— WRCCDC (@wrccdc) April 1, 2013
One last note to close with, like any effective team, we specialize. Our red team had an infrastructure specialist, folks going after web applications, some going after access via other means, and still others handling post-exploitation on Windows and UNIX. There really was a lot happening.