What type of reconnaissance do you do before a phishing attack? Recently, I was having dinner with new friends and inevitably, our conversation became a war story swap. One person started telling funny stories about calling help desk staff, trying to social engineer system information from them. I’m a lousy social engineer. When I was a kid, nothing would incur the wrath of my father quite like a lie. When I have to get system information, I prefer to use a system profiler.
A system profiler is a web application. This means, someone from your target’s organization must visit it. Once a visitor arrives, a system profiler uses a mix of Java and JavaScript to get information from the visitor’s browser. A system profiler logs which browser your target uses, which version of Windows, which version of Java, Adobe Reader, Apple QuickTime, Adobe Flash, and other popular plugins.
Once a system profiler gathers its information, it sends the target to another website.
The system profiler’s output helps you pick the right attack for your target. If you’re executing a targeted attack as an external actor, a system profiler is a must have tool.
Cobalt Strike includes a system profiler. Go to Attacks -> Web Drive-by -> System Profiler to start it. Fill in the URI to bind to and provide which website it should redirect visitors to. Press Launch and your system profiler is running.
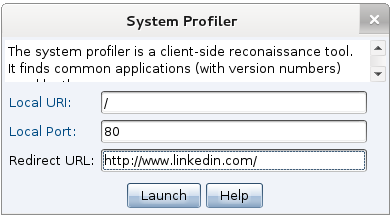
You don’t have to pay me for a system profiler. You can build your own. Visit http://www.browserspy.dk to see what’s possible.
Once you have a system profiler stood up, you need to get people to it. I like to send fake LinkedIn invitations to my system profiler targets. I edit a LinkedIn invitation message and change the identifying information to something false. When a target clicks my LinkedIn invitation, they visit my profiler. When my system profiler is done, it sends the target to linkedin.com like nothing ever happened.
I recommend that you send your system profiler link to a few targets–enough to get an idea of the diversity (or lack thereof) of workstation configurations. If someone reports your system profiler attack, this is a strong indicator to the IT staff that a phishing wave is coming. Remember–complacency is an attacker’s best friend, don’t ruin it.
Go to View -> Applications to see the system profiler’s output. This action will open a tab that lists each discovered application and its version information.
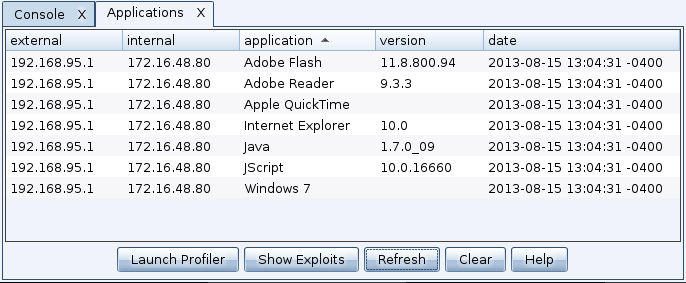
Now, let’s go through how to read a profile:
The internal IP address field is gathered from a benign unsigned Java applet. If this field says unknown, this means the Java applet did not run. If you see an IP address here, this means the unsigned Java applet ran. This is a useful clue to decide whether a Java attack is right for your follow-up attack or not.
Internet Explorer will report the base version the user installed. As Internet Explorer gets updates, the reported version information does not change. To find the patch level of Internet Explorer, it’s necessary to rely on contextual clues. One clue Cobalt Strike uses is the JScript.dll version. JScript.dll is Microsoft’s implementation of JavaScript. Its reported version changes with some Internet Explorer updates. To connect a JScript.dll version with an update, go to support.microsoft.com and search for the JScript version. This will give you an idea of which patch level to expect for Internet Explorer.
To see which exploits may apply, highlight an application in the System Profiler’s output and press Show Exploits. Cobalt Strike will do its best to show which exploits apply in the module browser. This feature takes into account contextual clues, like the JScript.dll version. Beware though, recommended exploits are not a list of what will work–it’s a list of what may work. This feature exists to help you start your search for the right attack.
My System Profiler does not, at this time, report whether a system or browser is x64 or x86. This information is very important when selecting an attack. You can still get this information though. Go to View -> Web Log in Cobalt Strike. Find the request for the System Profiler and look at the User Agent string the target’s browser sent.
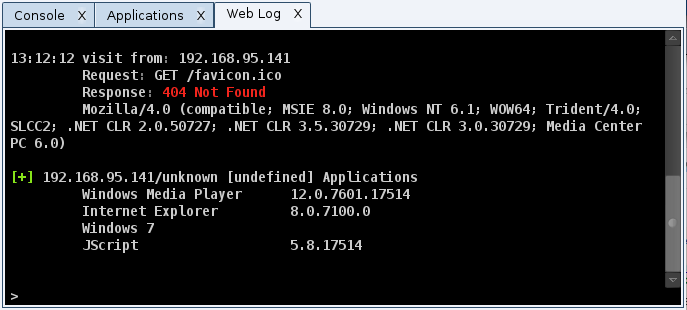
If you see the string WOW64 in the target’s browser user agent, then your target uses a 32-bit browser on an x64 system. WOW64 is Windows 32-bit on Windows 64-bit. It’s a compatibility layer to run 32-bit programs on 64-bit systems. By default, Windows 7 x64 is set up to use the 32-bit version of Internet Explorer.
If you see the string Win64 in the browser’s user agent, then your target uses a 64-bit browser on an x64 system. This is important to know, as this will change your attack options.
In my next Cobalt Strike update, I plan to make this x64 vs. x86 information part of the System Profiler’s output. For now though, it serves as a good reason to talk about how to analyze the User Agent string for more clues about your target’s system. — Update 08/21/13 – this is done now. Look for a *64 next to an application to indicate that it’s a 64-bit app.
Before I set up a client-side attack, I always gather a few system profiles first. I use the system profiler information to stage a virtual machine that matches my target’s workstation environment as closely as possible. I then try different attacks until I have a strike package I’m happy with. The trick to getting the most value out of a system profiler is knowing how to read it.
To learn more:
- David Kennedy and Kevin Mitnick coined the term system profiler in their Adaptive Penetration Testing talk at DerbyCon 2011.
- The classic Meta Phish paper talks about a Target Sieve which is functionally similar to a System Profiler. The Target Sieve differs in that it selects and directs the target to the best exploit. Cobalt Strike’s auto-exploit server is similar to a Target Sieve.