Last month, I announced Beacon’s ability to control a host over DNS. I see Beacon as a low and slow lifeline to get an active session, when it’s needed. Sometimes though, Beacon is all you have. There are times when Meterpreter gets caught too quickly or just can’t get past the network egress restrictions.
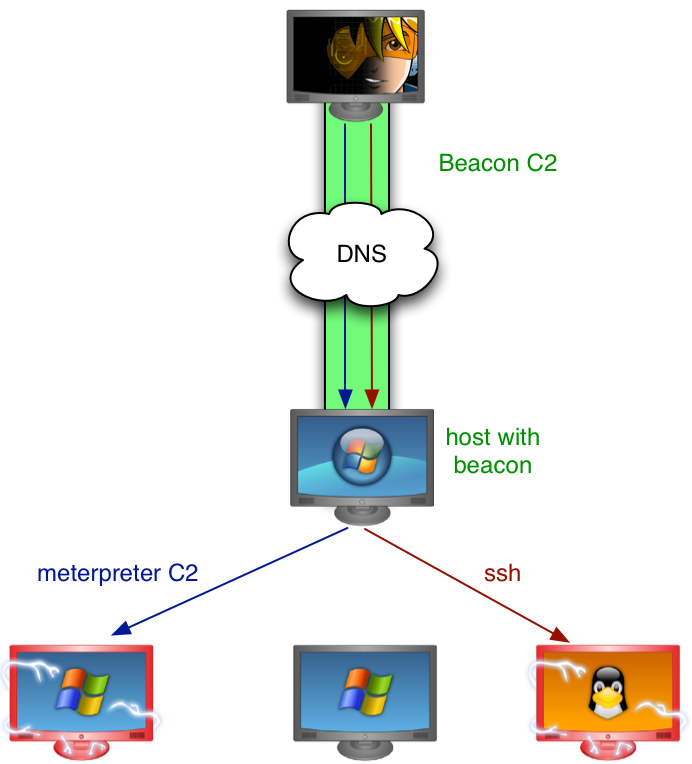
For these situations, Beacon has the basic post exploitation tools. Beacon can execute commands, get files, put files, log keystrokes, and inject shellcode to spawn another session. Today, Beacon can now act as a pivot to relay your scans and attacks into a compromised network. If you can’t get a Meterpreter session or if Beacon’s DNS channel is your only way out, it’s now possible to continue your march into your target’s network.
Setup
To pivot through a Beacon, go to View -> Beacons, and interact with the Beacon you would like to pivot through. First, you will want to decide on the right data channel. Cobalt Strike’s DNS Beacon gives you three options:
Use mode http to ask Beacon to use HTTP as a data channel. When it’s time to checkin, Beacon will connect to you and download tasks as an HTTP GET request. When there’s data to send back, Beacon will use an HTTP POST request to send data. This option is the default data channel. It is also very fast and has much more capacity than both of the DNS data channels.
Use mode dns to ask Beacon to use DNS as a data channel. When it’s time to checkin, Beacon will make several A record requests for a domain your Cobalt Strike system is authoritative for. Each request will download 4 bytes of the tasking at a time. Data is sent back as a series of A record requests with data embedded in the requested hostname.
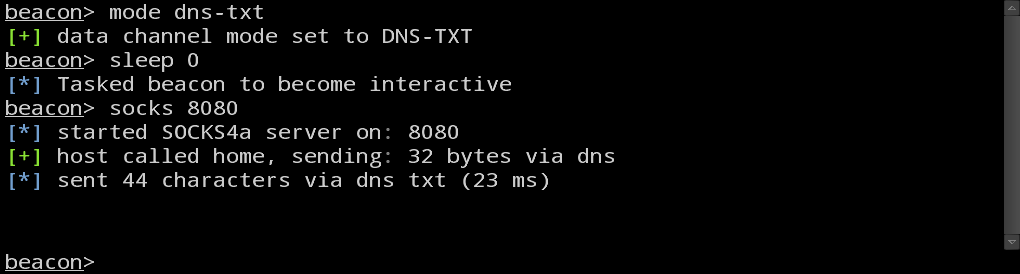
The normal DNS mode is sufficient for controlling a compromised host, but for pivoting, 4 bytes per DNS request is not a lot of capacity. To make up for this shortcoming, I’ve added mode dns-txt which asks Beacon to use DNS as a data channel, but download tasks using TXT records. This gives Beacon a capacity of ~184 bytes of base64 encoded data per request. If you’d like to use Beacon to relay traffic over DNS, I recommend that you use this mode first.
Next, you will want to change want to change Beacon’s sleep time. By default, Beacon calls home every sixty seconds. When relaying traffic through Beacon, this sleep time introduces unnecessary latency. Use sleep 0 to task Beacon to call home several times a second.
Now, type socks 8080 to set up a SOCKS4 proxy server on port 8080. Beacon exposes its pivoting capability as a SOCKS proxy server. This gives you the freedom to relay traffic from the Metasploit Framework, proxy aware tools and external tools.
Your Beacon console should look something like this:
Metasploit Framework Setup
To relay the Metasploit Framework’s traffic through Beacon, go to View -> Console, and type: setg Proxies socks4:127.0.0.1:8080. This option will force the Metasploit Framework to route outgoing TCP connections through the Beacon SOCKS proxy server. Once this option is set, you may launch modules and interact with the Metasploit Framework through Cobalt Strike.
To stop relaying new connections through Beacon, use unsetg Proxies to unset this global option.
Host Discovery and Enumeration
If you have a foothold on a system and you can’t or don’t want to create a Meterpreter session, you will have to find some way to discover hosts before launching a scan through Cobalt Strike. Use Beacon to run ipconfig against the compromised system to learn the basics of the network you’re on. Issue an arp -a command to see which hosts are in the ARP cache and add them to the database (Hosts -> Add).
Next, to discover some low hanging fruit type hosts, launch the auxiliary/scanner/smb/smb_version module against the network your compromised host is on. If you’re using DNS as a data channel, I recommend running one scan at a time to keep the channel responsive and avoid any unneeded timeouts. Once the smb_version module completes, follow it up with auxiliary/scanner/ssh/ssh_version. If there are other services you’re interested in, launch these modules against the network too.
Once you’ve identified a handful of hosts, you may highlight them in the targets area, right-click and select Scan to learn more about them.
Exploitation
Once you have some target information, presumably you know which attacks you’d like to try. You can launch exploits through a Beacon pivot, use psexec, or launch an auxiliary module like ssh_login.
Here are a few details to keep in mind:
- If you launch an exploit through a Beacon SOCKS pivot, you may use a reverse connection, but you must set the Metasploit Framework option ReverseAllowProxy to true. Use setg ReverseAllowProxy true. Beware that the reverse connection will attempt to come back to you or the LHOST you specify directly. The Beacon SOCKS proxy server does support the ability to set up a listening socket (its part of the SOCKS protocol), but I do not know how to force the Metasploit Framework to take advantage of this.
- You may use a bind payload through a Beacon SOCKS pivot. Beware that Meterpreter is big and staging a ~750KB payload over DNS TXT records takes a few minutes (not to mention, it’s a lot of requests too). If the target network can communicate with you over HTTP, use mode http to force Beacon to communicate with you using HTTP GET and POST requests. Launch your exploits, get your meterpreter sessions, and then use mode dns-txt to happily manage your meterpreter sessions through a DNS channel. Changing the communication mode of Beacon will not drop or otherwise affect connections relayed through the Beacon. This gives you a lot of flexibility to use the right channel for the right situation.
- Cobalt Strike bundles all data it must relay via Beacon into one package. Once this data is transmitted to your Beacon (through whatever channel), this data is parsed, and sent to the right sockets. If you have a large transfer taking place (*cough*staging meterpreter*cough*) over a DNS channel, expect your other connections to become non-responsive until the transfer is complete. Beware of the capacity of the channel that you’re using when pivoting through Beacon.
This new ability to pivot through Beacon gives Cobalt Strike users egress options that they did not have before. This ability to pivot through Beacon is available in today’s Cobalt Strike update. Licensed users may get the latest release with this feature by running the built-in update program. A full list of changes are in the release notes.