In June 2012, I released Cobalt Strike, a commercial penetration testing package that picks up where Armitage leaves off. Cobalt Strike is a direct expression of what I think a penetration test looks like. If you’re interested in this vision, this post will walk you through it.
The term penetration test is overloaded and may mean something different with each person that you ask to define it. To some people, a penetration test is a vulnerability verification exercise. To others, it’s an expert using the tactics and techniques of a skilled adversary to assess a mature security program’s ability to cope with a targeted attack.
I used to work as a contractor, providing red team services to a DoD customer. I saw gaps between the abilities of my tools and what I had to do. There isn’t much help for those of us who have to execute a full-scope external engagement. I wrote Cobalt Strike to fill the gaps I saw. Cobalt Strike is a tool execute a targeted attack. Let’s go through what a targeted attack looks like.
Reconnaissance
We’ll start where the active part of a penetration test begins, reconnaissance. Cobalt Strike’s system profiler is a web application to probe and report the client-side attack surface of anyone who visits it. The system profiler reports the applications a user is running along with version information. This report isn’t comprehensive. The system profiler can’t discover all applications, but it does discover the common ones that attackers target. I liken this to the client-side version of a port scan with a banner grab.
Once you have a system profile, you can plan an attack. If your client doesn’t allow client-side attacks, that’s fine. A system profile alone is enough to generate a client-side vulnerability report. If you’re allowed to go further, the tools are there.
Access
Cobalt Strike recommends client-side exploits based on a system profile. You may choose to use one of these exploits in your targeted attack. You have one problem though. The client-side exploits in the Metasploit Framework are caught by most anti-virus products. I don’t blame the Metasploit Framework for this. The project does not promise anti-virus evasion. This is a problem that’s up to the user to solve.
If you want to deliver a client-side memory corruption exploit, that’s fine. Set up a virtual machine and install the anti-virus product your target uses. Change obvious strings in the Metasploit module until it passes the anti-virus product you’re interested in. Cobalt Strike will happily use your modified Metasploit Framework modules.
Java Drive-by Exploits
Lately, the client-side whipping boy is Java. Several Java attacks disable the Java security sandbox and allow an attacker to silently execute code without alerting the user. These attacks are extremely reliable and do not rely on memory corruption. If the user’s Java is patched, you may deliver a signed Java applet to a user and hope they give your applet permission to run without restrictions. This is a staple social engineering attack.
This week’s Java 1.7u11 release makes some attempts to mitigate Java attacks in a generic way. We’ll see how much the new security settings affect penetration testers. You may find a target is running an outdated Java, giving you a free pass into their system. You may find your target is up to date and this may influence your attack strategy.
If you do choose to use a Java attack, know that there is a downside. The Metasploit Framework’s Java exploits are tightly coupled to a few payload options with no randomization at all. Popular anti-virus products detect the Java exploits and payloads. There is no option to use an anti-virus safe Jar file with a Java exploit module.
If you want to use a Java attack in a penetration test, you must reimplement it and host it yourself. I did this for you. Cobalt Strike includes an implementation of the signed Java applet attack. I also include a Smart Applet attack that detects the current version of Java and disables the security sandbox with an exploit before it executes your payload. If you want something intelligent, start the Web Drive-by Exploit server and tell it to use Java attacks only. With this feature, Cobalt Strike will detect the version of Java a visitor has and deploy the Smart Applet attack if it makes sense or fall back to the Signed Applet.
Of course, there’s another problem: anti-virus. It’s only a matter of time before every anti-virus product on the planet screams at the sight of my Java attack kit. For my customers, I provide a small SDK with the source code to Cobalt Strike’s Applet Kit. The build files are there. Modify the code as you see fit and rebuild it. Load an included Cortana script to make Cobalt Strike use your changes. This collection of source code, ready to tweak for AV evasion, is the Cobalt Strike arsenal.
Hacking with Features
Exploits aside, there’s another class of attacks well supported by Cobalt Strike: features. I expose several gems in the Metasploit Framework to add a Macro to Word and Excel files, generate a Java JAR file, or trojanize a Windows executable. If there’s no exploitation opportunity, use Cobalt Strike to add an agent to a regular file.
At this point, you have a package that will execute code on workstation. Great! Now, let’s make this package into something that won’t raise suspicion. You can register a domain and setup a fake website that plays to your pretext. If you’re in a hurry, use Cobalt Strike’s website clone tool to clone a site and embed your attack into it.
Spear Phishing
Now, you need to get the attack to the user. Spear phishing is a common way. Let’s talk about that. Most penetration testers have a dust-covered Perl script that will connect to a mail server and deliver a message. This piece is trivial to do. The hard part is crafting a message that matches your pretext. No matter how hard any tool developer tries, our hacking tools can’t and should not try to replace a modern email client to compose a message. If this sounds out of left field, stay with me for a minute.
A successful spear phishing attack requires a good pretext. Period. The pretext is the ruse you create to convince a user to open your attack package and give you access to that system. In your pretext, someone is sending the message. This person works for an organization. They have a signature block, they use certain fonts in their message, they may have that stupid legal notice at the bottom. Whatever it is, you should base your phish on a real message. If you have a message from that person, save it and edit it in a text editor to say what you want. If the phish’s sender isn’t real, compose a message in an email client and send it to yourself. In both cases, you have a message composed in an email program that looks right and says what it needs to support your pretext.
Now, you need to repurpose this message and get it to the user. This is where Cobalt Strike helps. Its spear phishing tool imports saved email messages. Import the message and Cobalt Strike will strip most of the headers from it. Cobalt Strike will also replace all links in the message with a link to your attack package. If you want to attach a file, that’s OK too.
Cobalt Strike’s spear phishing tool communicates directly with your target’s external mail server to deliver the message. If you have a mail server that will deliver messages, give Cobalt Strike the details to authenticate to it and Cobalt Strike will use this option instead.
Command and Control
Now, you have a package that will give you code execution, pass host anti-virus, and a way to deliver it. What else is there? Command and control.
If you get code execution on a user’s system, you need a way for their system to communicate with you. This is necessary if you’re going to take data from the system or use it as a hop point for other attacks
One option is Meterpreter. Its reverse HTTP[S] payloads will communicate through a transparent proxy. Its reverse TCP payload will connect to you on an any port you choose. Cobalt Strike supports these options.
An alternative is Cobalt Strike’s Beacon payload. Beacon works like some of the advanced malware in the wild. Once it’s staged, it limits its communication to you. Beacon will make a DNS request using the resolver built into Windows. It will ask if a host exists on one of several domains you control. If the host exists, Beacon uses this as a signal to phone home and request a task. If the domain doesn’t exist, Beacon goes to sleep. To manage this, Cobalt Strike ships with its own DNS server. You simply point the NS records to your attacker system and Cobalt Strike takes care of the rest.
Beacon is the tool to maintain a foothold in a network. Beacon has a few post exploitation capabilities too. It will log keystrokes, execute commands, and inject shellcode into memory. With Beacon in place, you may give yourself a Meterpreter session when you’re ready to use it.
As a placeholder, Beacon has several advantages over Meterpreter. It’s not chatty. It communicates with you on a set interval. The DNS variation of Beacon, will not communicate with you unless there is a task. Further, you may deploy Beacon with multiple domains embedded inside of it. If one of your domains is blocked, Beacon will still reach you through the others. This makes your placeholder more resilient. These capabilities make Beacon desirable for your first access. You don’t want to go to the trouble to get an access and then lose it because Meterpreter crashed or your attacker IP was blocked.
Post Exploitation
For post-exploitation, Cobalt Strike offers the same tools as Armitage to control Meterpreter. You can setup proxy pivots, launch privilege escalation exploits, download and upload files, take screenshots, and interact with a command shell. As an added bonus, you can automate your post-exploitation activity using Cortana scripts. Cortana is the scripting technology paid for by DARPA’s Cyber Fast Track program. It’s open source. You can use Cortana scripts with Armitage or Co
balt Strike.
During a targeted attack, another problem arises that Cobalt Strike is well suited for. It’s likely you have one or two accesses into a network and multiple teammates. I built Cobalt Strike’s tools into Armitage because I saw a natural complement here. Armitage is a solid foundation for red team collaboration. You may communicate activity in a chatroom, share sessions, and have access to the same data as your teammates. Now, those one or two sessions aren’t a problem. Your team, each member with a different job to do, can set to work on the target’s network by sharing those accesses. If a penetration tester encounters a system they don’t have the knowledge to deal with, a specialist can connect to the teamserver and set to work from the position in the network you worked hard to get.
Lateral Movement
It’s unlikely that the system you land on is your destination. Once you have a foothold in a network, you will need to attack other hosts. With Armitage and Cobalt Strike, you can set up a pivot through Meterpreter, discover and scan hosts, and launch remote exploits. While this is nice, the juicy stuff is abusing trust relationships.
Lateral movement in a network involves abusing your position of trust to compromise otherwise patched hosts. In an active directory network, you simply authenticate to a host, copy an executable to it, and schedule this executable to run. To authenticate to a Windows host, there are three artifacts that will help you: tokens, password hashes, and plaintext passwords.
Token Stealing
In Windows, every thread has an access token associated with it. This token acts as a cookie to identify the user, their groups, and the privileges the token holds. If an attacker controlled thread has a token for say, a domain administrator, then the attacker may do anything that the domain administrator user can do. These actions aren’t restricted to local actions either. You can execute commands to interrogate a host, list files, and move files between hosts. Why, you can even schedule tasks if you’re an administrator.
Meterpreter has a lot of functionality for listing and stealing tokens. Both Armitage and Cobalt Strike have dialogs to manage this functionality. You can steal a token directly from a process–this gives your meterpreter session the rights of that user or you can list all tokens available on the system and impersonate one of them.
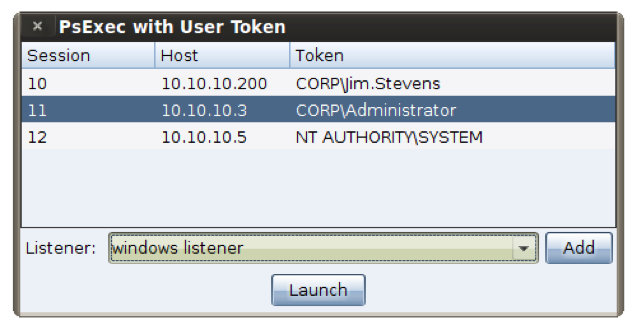
To move laterally with a token, Cobalt Strike provides a dialog for the Metasploit Framework’s psexec with current user token module. This dialog lists all meterpreter sessions you have and which token is associated with each. Simply select one and the Metasploit Framework will create a share through the meterpreter session you select and ask the target hosts to schedule a job to execute a program hosted in that share.
The phrase execute a program should raise a red flag and signal alarm bells in your head. This is an opportunity for our very dear friend anti-virus to stop us. If you rely on the executable generated by the Metasploit Framework, you’re caught.
Cobalt Strike’s psexec dialogs allow you to specify any executable that you’d like. This saves you from the executable generated by the Metasploit Framework, but it forces you to step away from the flow of the penetration test and work on crafting an executable that anti-virus doesn’t catch.
Another option is to load a Cortana script that intercepts any psexec actions, extracts your payload parameters, and generates an AV-safe executable for you. I wrote a generic HOWTO on anti-virus evasion with Cortana awhile ago. For Cobalt Strike customers, I went a step further. I wrote a simple AV by-pass executable and made it and its source code available in the Cobalt Strike arsenal.
Pass-the-Hash
Cobalt Strike and Armitage expose Meterpreter’s ability to extract password hashes if you’re SYSTEM on a host. You may use the password hash to login to a host, copy an executable, and schedule it to run. This is the pass-the-hash attack. It works because the password hash is not salted and it’s all you need to authenticate to a host with. This doesn’t work with all users though. You need a password hash for a local administrator or domain administrator user.
Fun with Passwords
If you manage to get plaintext credentials, you can use them with Cobalt Strike’s psexec dialog, the same as you would use password hashes. One way to get plaintext password is to log keystrokes. I built the keystroke logger into Beacon for this purpose. Beacon’s keystroke logger tracks the active window with the current keystrokes.
Separate from Cobalt Strike, there are two innovative programs you should know about: mimikatz and Windows Credential Editor. These programs will grab cached Windows user credentials from memory for you. I’d include either of these programs in Cobalt Strike if I could work out a licensing deal with either author. In the meantime, you can use Cortana to integrate either of these tools into Cobalt Strike. I wrote a script for Windows Credential Editor already. The freedom to integrate external tools with Cortana is one of Cobalt Strike’s strengths.
Plaintext credentials are the best thing that can happen to you. You may use them to login to internal web applications, servers, maybe access a VPN for employees, or use RDP. The sooner you can dump hacking tools and switch to normal administration tools–the better.
VPN Pivoting
Once you’re inside a network, there’s a lot more you can do. You can sniff traffic and attempt to capture information that way. You can host a rogue smb server and use it to capture or relay the credentials of any system that touches your server. There’s a lot of opportunity that opens up.
Unfortunately, these opportunities require being inside the network. Layer 2 access, as if your system is plugged into that network.
Cobalt Strike can help you here. Its Covert VPN feature bridges you into your target’s network using a compromised Windows workstation as a hop point. How does it work? Think of it as a two-way packet sniffer. Covert VPN sets up a network interface on your attacker system. Anything that passes through this interface is dumped as-is on your target’s network. On the compromised host, acting as a relay, any frames it sees are made available to the network interface created by Covert VPN.
The covert part of Covert VPN is the ability to choose how it relays traffic back and forth. You can relay frames using a UDP transport. This is fast and works like a traditional VPN. You can relay frames using a reverse TCP connection. Or, you can relay frames as HTTP GET and POST requests. This last option is useful if the only way out of a network is through a proxy server. None of these options is very quiet though, a VPN is always chatty.
With Covert VPN, you have the option to bring other tools into your engagement. You’re now in the target’s network and can do what you need to do.
Epilogue
This is where Cobalt Strike will take you to. We started at the beginning of an attack, the reconnaissance phase. I showed you how a system profiler will help you gather the information necessary to execute an attack. We talked about attack options and anti-virus evasion. We then brought spear phishing into the picture. Once you gained a foothold, I discussed how to abuse it to spy on the user and to abuse your position in the network to attack other hosts. From the perspective of Cobalt Strike, this is how you hack into a typical enterprise network.