Listeners are Cobalt Strike’s abstraction in front of the Metasploit Framework’s payload handlers. A handler is the exploit/multi/handler module. This module sets up a server that waits for a payload on a compromised system to connect to you.
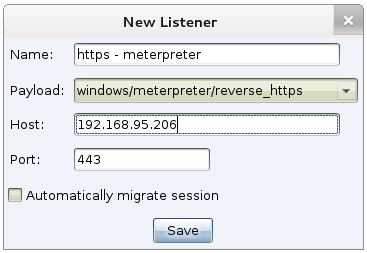
Cobalt Strike’s listeners feature is a way to configure handlers that start when Cobalt Strike starts. A listener consists of a user-defined name, a payload, a host, a port, and whether or not you would like the payload to automatically migrate.
Many Cobalt Strike features let you choose a listener to quickly configure a payload. When you take advantage of this, you’re certain that the information is correct. Here are the ways you can use listeners:
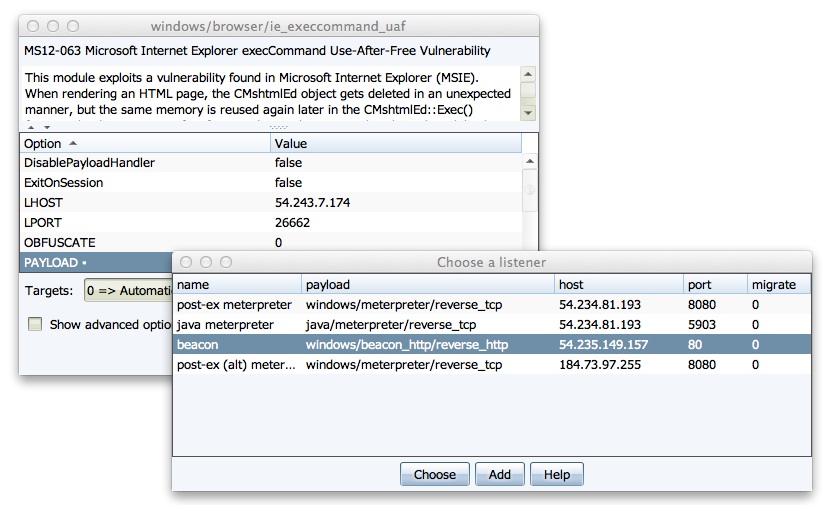
- You can quickly configure a Metasploit Framework exploit to use a pre-defined listener. Double-click the PAYLOAD option to choose one of your listeners. This action will populate the module’s options for you.
- When you task a Cobalt Strike Beacon to spawn a session—you get to choose a listener from any of the Cobalt Strike team servers you’re connected to. This is an incredibly seamless way to pass shells to different team servers.
- All Cobalt Strike social engineering packages allow you to choose a listener to pair with the attack.
Listeners are an abstraction. They’re the one-stop shop to set up handlers in Cobalt Strike. Given that this convention works well—Cobalt Strike’s Listener Management feature becomes the place to hook in Cobalt Strike-specific stuff.
Beacon is a good example of this. To Cobalt Strike users–Beacon feels like a first-class payload. It’s not an external tool or something that is awkwardly integrated. Beacon doesn’t exist in the Metasploit Framework though. It’s a Cobalt Strike payload that stages as the windows/dllinject/reverse_http payload when used with a Metasploit Framework feature. Listeners made it possible for me to define Beacon as a payload alongside Meterpreter’s various options.
Listeners are also my opportunity to expose some hidden functionality in the Metasploit Framework to my users. For example, not many people know that it’s possible to tunnel reverse_tcp payloads through a Meterpreter session. Cobalt Strike helps you do this through pivot listeners.
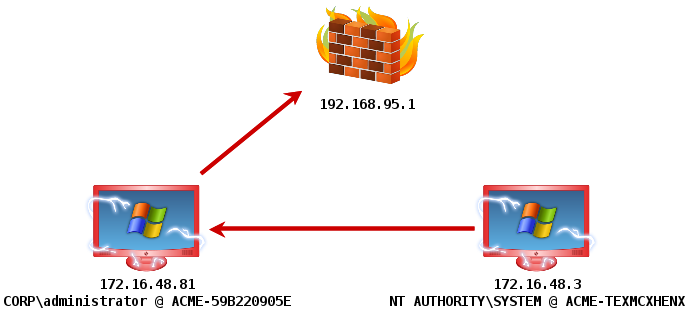
A Pivot Listener is a listener that is set up to route back to you through a Meterpreter session. This is really an incredible feature. A lot of privilege escalation actions will spawn a new session. If I care at all about stealth—I want to make as few outbound connections from a compromised system as possible. With a Pivot Listener—I can generate Cobalt Strike EXEs and DLLs that tunnel through an existing session. This is very powerful. Once the listener is set up, I just use it without having to recall the details behind it.
Cobalt Strike’s Listeners also setup stage encoding for Windows payloads as well. Once you get code execution, the stub of code sent with the attack downloads the rest of the payload to inject into memory. This transaction is easy to catch as the downloaded payload is a DLL with a little bootstrap code prepended to it. For nearly a year now, Cobalt Strike’s Listeners have helped users avoid detection by setting up stage encoding for them.
Listeners also make it possible to enjoy a wider variety of Metasploit Framework payloads. For example, if I want to do callbacks over IPv6, I can configure an IPv6 listener and provide it the right LHOST once. I don’t have to remember my IPv6 address every time I set LHOST. Cobalt Strike’s Listener keeps track of this information for me.
Listeners make Cobalt Strike redirector friendly too. A redirector is a server with iptables rules or port forwarding software that sends traffic to your attack server. Once you have redirector infrastructure setup—you can create Cobalt Strike listeners that call home to it. Redirectors are a way to obfuscate the true location of your attack server. You may assign a different redirector to each listener you create. After this initial setup, it just works. Cobalt Strike’s Beacon payload may also stage through a redirector and call home through multiple redirectors.
One danger with an abstraction, like Cobalt Strike’s listeners, is that they hide some output and information from you. Cobalt Strike mitigates this by making it possible for you to watch the output of any Metasploit Framework handler managed this way. Go to Cobalt Strike -> Listeners, right-click the listener, and choose Debug. Cobalt Strike will stop the handler and start it again in its own console. Through this console, you may see all output associated with that handler.
Listeners are the glue that holds Cobalt Strike together. They allow seamless cooperation between team servers, use of redirectors, and they save you and your team the trouble of remembering the configuration information for these shared assets.
If you’d like to learn more about Cobalt Strike’s listeners, review the documentation or watch Part 3 of the Tradecraft course.