So, I just realized there isn’t a modern tutorial on how to start Armitage and take advantage of it. There’s the documentation, but my documentation tries to cover every corner case and it’s not friendly to the novice who wants to try it out quickly. I do not know of a getting started guide that is up to date with the latest Armitage conventions. This blog post is my attempt to correct this oversight.
22 May 2013 – I’ve updated this tutorial to state how to use Armitage with Kali Linux, since BackTrack Linux is no longer supported.
22 Sept 2013 – Added instructions to make Kali Linux use Java 1.7 by default. The Java 1.6 shipped with Kali causes graphical glitches.
16 April 2014 – This blog post is still good advice. If you’re looking to get started with Armitage, you’re reading the most modern and complete guide.
What is Armitage?
Armitage is a graphical user interface for the Metasploit Framework. At first glance, it may seem that Armitage is just a pretty front-end on top of Metasploit. That’s not quite true. Armitage is a scriptable red team collaboration tool. It has a server component to allow a team of hackers to share their accesses to compromised hosts.
It’s also possible to write bots that connect to this team server and extend Armitage with scripts written in a language called Cortana. This Cortana piece was funded by DARPA’s Cyber Fast Track program. There’s a lot here.
Armitage (Fast and Easy Hacking)
Multi-Player Metasploit with Armitage
If you aren’t familiar with the Metasploit Project, it’s an open source collection of safe and vetted exploits. Once an exploit makes it into the Metasploit Framework, it’s immediately available to its ~250K users. The Metasploit Framework isn’t just exploits though, it’s an integration point for offensive capabilities that simply work together. It’s also very easy to hook your own stuff into it.
There are several programs that build on the Metasploit Framework and take advantage of it. For example, Rapid7, the company that employs Metasploit’s founder and its core team, has a line of penetration testing products built on the framework. The subject of this tutorial is the open source Armitage GUI, which I wrote. I also develop Cobalt Strike, which adds threat emulation tools to Armitage.
If you work in security or have an interest in it, you owe it to yourself to spend some time learning about Armitage and the Metasploit Framework and how to use them.
Let’s dive in.
Starting Kali Linux
The best way to start playing with Armitage is to download Kali Linux and run it in a virtual machine. For this guide, you should set your virtual machine to NAT networking. This is necessary because in a moment, I will ask you to download a target virtual machine and set it up.
To login to Kali Linux, use the username root, password toor. To request an IP address via DHCP, type dhclient. To start X Windows, type startx.
Use Java 1.7
Kali Linux ships with Java 1.6 and Java 1.7. Java 1.6 is the default though and for some people–this version of Java makes their menus stick or draw slowly. For the best Armitage experience, you should use Java 1.7. Fortunately, it’s one command to change the default.
If you have 32-bit Kali Linux, open a terminal and type:
update-java-alternatives --jre -s java-1.7.0-openjdk-i386
If you have 64-bit Kali Linux, open a terminal and type:
update-java-alternatives --jre -s java-1.7.0-openjdk-amd64
Installing Armitage
Your version of Kali Linux may not include Armitage. To install it, type:
apt-get install armitage
Next, you need to start the Metasploit service. Armitage does not use the Metasploit service, but starting it once will setup a database.yml file for your system. This is a necessary step. You only need to do this once:
service metasploit start service metasploit stop
Updating the Metasploit Framework
Use the msfupdate command to update the Metasploit Framework to the latest. Armitage is included with the Metasploit Framework, so it will update too (not any more).
Starting Armitage
Before you can use Armitage, you must start the postgresql database. This does not happen on boot, so you must run this command each time you restart Kali:
service postgresql start
To start Armitage in Kali Linux, open a terminal and type:
armitage
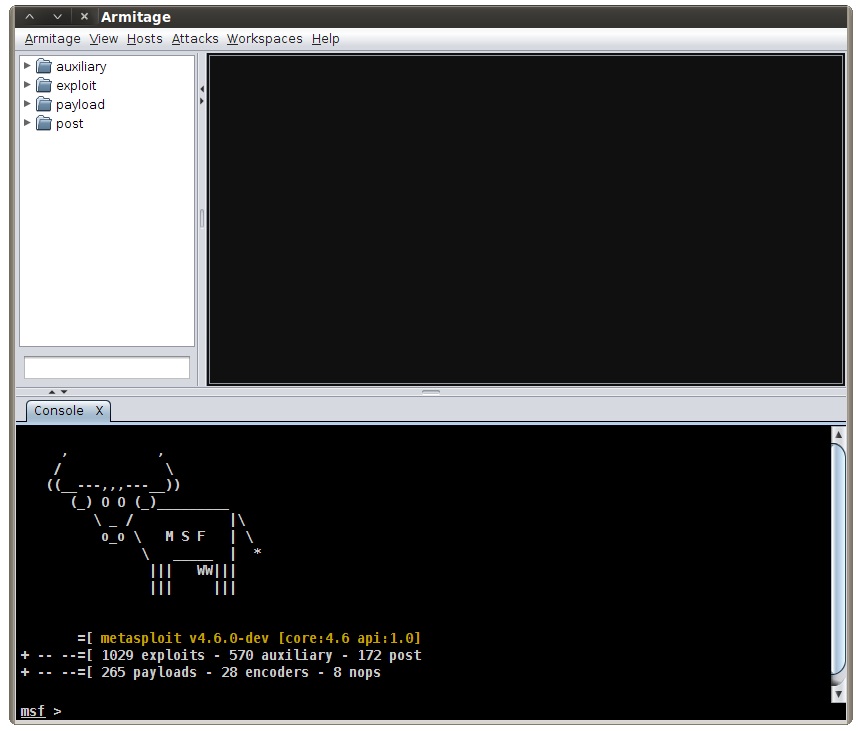
Armitage will immediately pop up a dialog and ask where you would like to connect to. These parameters only matter if you want to connect to an Armitage team server. Since we’re getting started, we don’t care. Just press Connect.
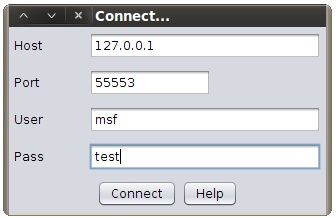
Next, Armitage will try to connect to the Metasploit Framework. Big surprise, the Metasploit Framework is not running. Armitage will realize this and it will ask you if you would like it to start Metasploit for you. The correct answer is Yes. Press this button and wait.
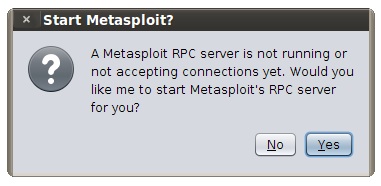
You will see connection refused messages for up to a few minutes. If this is your first time starting the Metasploit Framework, this may take literally a few minutes. The Metasploit Framework is the largest Ruby codebase out there and it takes time to load all of its modules for the first time. Be patient.
If all went well, you will see a GUI that looks like this:
You’re now ready to use Armitage.
A Target
Every attacker needs a target. Since you’re just starting out, I recommend that you set up a target virtual machine made for learning the Metasploit Framework. If you need such a target virtual machine, look no further than Metasploitable 2.
Metasploitable 2 is a virtual machine maintained by the Metasploit project team. It’s an Ubuntu server with a lot of services and vulnerabilities.
You can download Metasploitable 2 at:
http://sourceforge.net/projects/metasploitable/files/Metasploitable2/
Set this virtual machine up. Make sure you set the networking for this virtual machine to NAT or host-only. You do not want to expose this virtual machine to the internet.
To learn its IP address, login as user msfadmin, password msfadmin when this virtual machine starts up. Type ifconfig to see the network configuration for this virtual machine. Once you have an IP address for this system, you’re now to ready to attack it.
Now, go RTFM
The Metasploit Framework has a lot of jargon and Armitage has a lot of conventions associated with it. Now that you’re up and running, I recommend that you take a few minutes and read the Armitage manual. You can skip the Getting Started portion if you like. Pay special attention to section 1.4 which details some of the vocabulary around the Metasploit Framework. I also recommend that you read the User Interface Tour, Exploitation, and Post Exploitation chapters.
The Armitage manual is not a tutorial, but it will help orient you around the tool. You want this orientation, because in the next part of this guide, you will attack the Metasploitable Virtual Machine that you setup a moment ago.
Armitage Labs
I spend a lot of time teaching folks how to use Armitage and its big brother Cobalt Strike. To start out right, I have my students go through several labs designed to help them experience the conventions in the Metasploit Framework first hand. Work through these labs and you will start to develop a mental model of what the Metasploit Framework can do and how it’s organized.
Scan
- Go to Hosts -> Nmap Scan -> Intense Scan, all TCP ports
- Type the IP address of the Metasploitable Virtual Machine
Wait for the scan to complete. It will take some time. - Right-click the Metasploitable host and select Services
Exploit
- Go to Attacks -> Find Attacks
- Wait for Attack Analysis complete dialog.
- Right-click the Metasploitable host and try various items from the Attack menu until one works. Something is bound to work.Right-click the Metasploitable host and select Shell 1 -> Interact. If you have a Meterpreter 1 menu, then keep searching. Meterpreter is a great post-exploitation tool, but we’re not ready to talk about it yet. Find an exploit that yields a shell.
- Type: whoami and press enter in the new Shell 1 tab.
Brute Force VNC
- Select the Metasploitable host in the target area
- Navigate to auxiliary -> scanner -> vnc -> vnc_login in the module browser. Double-click this module.
- Press Launch
- Open a Terminal and type: vncviewer metasploitable IP:5900. Use the password vnc_login helped you discover to connect.
Tomcat Manager Deploy Exploit
- Select the Metasploitable host in the target area
- Navigate to auxiliary-> scanner -> http -> tomcat_mgr_login in the module browser. Double-click this module.
- Double-click the RPORT value and change it to the correct port. Take a look at the services on the system. Which port is running Apache Tomcat?
- Press Launch
- Navigate to exploit -> multi -> http -> tomcat_mgr_deploy in the module browser. Double-click this module
- Change RPORT, USERNAME, and PASSWORD to their correct values. Step 4 should have yielded a valid username and password for you.
- Press Launch
Brute Force
Metasploit modules ending with _login are usually able to brute force credentials. Try mapping one of the open services to its login module and follow these steps:
- Type _login in the search box below the module browser
- Launch the *_login module you’re interested in. Type _login in the box below the module browser to search for these modules
- Find the USER_FILE option and double-click the black square. The black square indicates that there is a helper dialog to set this option
- Double-click on the wordlists folder
- Choose the unix_users.txt file
- Set the PASSWORD option to something silly, such as password. Or, set PASS_FILE to a juicy looking file (but then expect this to take a long time)
- Press LaunchHow many weak accounts did you find?
Postgres Ownership
Not all vulnerabilities will yield a shell. That’s OK. Sometimes there are other great opportunities:
- Try to brute force credentials to the postgres database running on the system
- Use the results of step 1 to read the contents of /etc/passwd through the postgres database. Hint: search for any postgres related modules. There may be one that can help you.
Where to go from here?
If you made it this far, you’ve started Armitage, started a target, and had a chance to experience these tools first hand. If you’d like to learn more about Armitage, I recommend that you watch the free Armitage and Metasploit Training Course at ethicalhacker.net.
If you’re interested in a deep dive on the Metasploit Framework, the standard reference is the Metasploit Unleashed Course. If you’d like a book, read Metasploit: The Penetration Tester’s Guide, and if you like videos, I recommend Vivek’s Security Tube Metasploit Framework Expert Series.
If you’re a professional penetration tester and Armitage piques your interest, I would also like to point you towards Cobalt Strike. Cobalt Strike is a toolset for red team operations and adversary simulations. Cobalt Strike’s 3.0 release no longer depends on the Metasploit Framework. It’s a stand-alone toolset, separate from Armitage. Use Cobalt Strike in situations where you need to work as an external actor and stealth matters a great deal.
Enjoy