For a long time, I’ve wanted the ability to use PowerUp, Veil PowerView, and PowerSploit with Cobalt Strike. These are useful post-exploitation capabilities written in PowerShell.
You’d think that it’s easy to run a script during the post-exploitation phase, especially when this script is written in the native scripting environment for Windows. It’s harder than you’d expect. Existing options require one-liners that Invoke-Module a local file or grab a script from a third-party web server. This hurdle prevents non-PowerShell developers from seeing what’s possible.
During this last development cycle, I decided to work on this problem. Beacon now runs your PowerShell post-exploitation scripts. This feature does not touch disk and it does not connect to an external host or site.
Here’s how to use it:
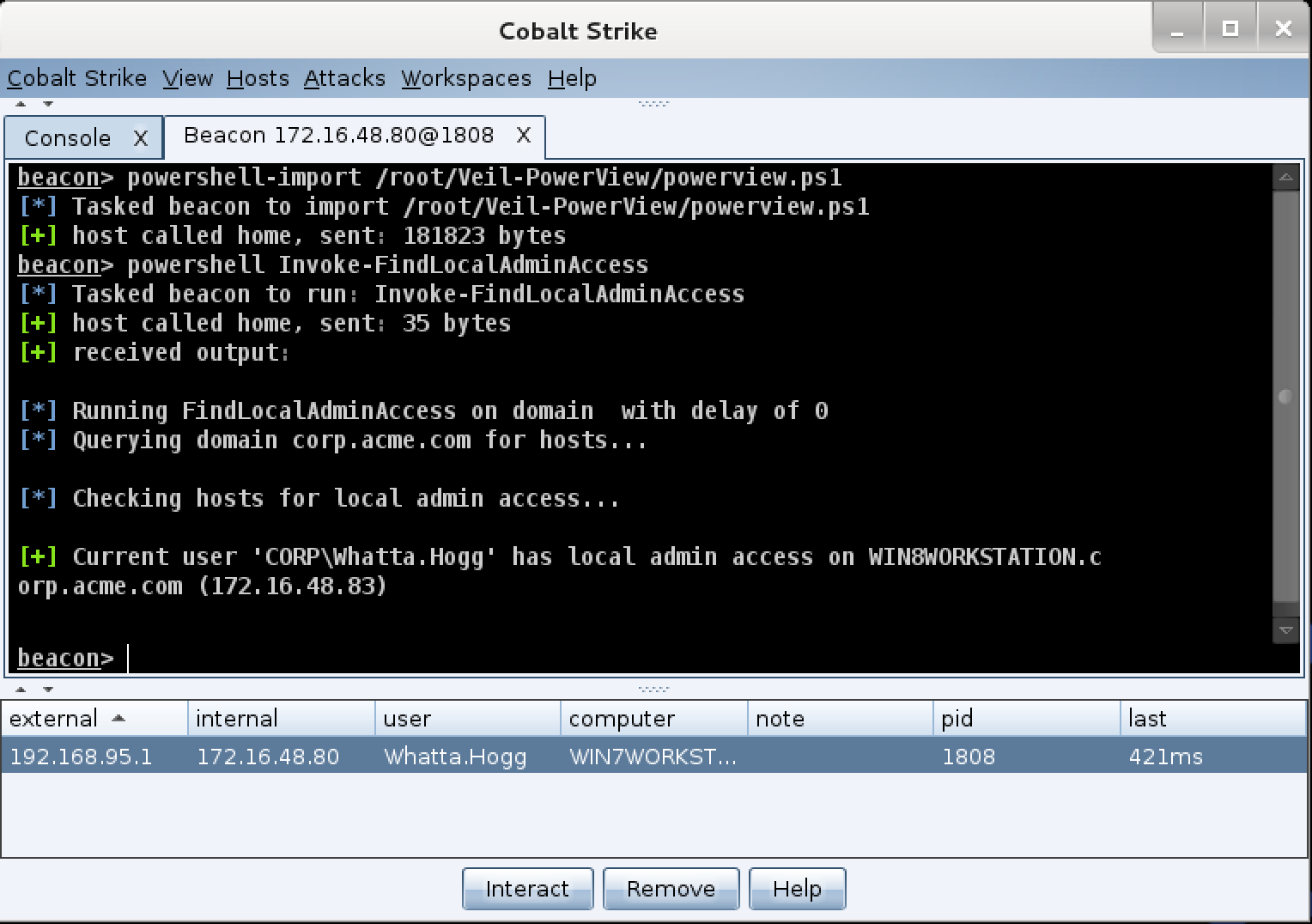
The powershell-import command loads a PowerShell script into Beacon. This script stays in memory for the duration of the Beacon session.
Use the powershell command to invoke expressions and cmdlets that reference the contents of the imported script. You may also tab complete cmdlets from the imported script with the powershell command too.
This video demonstrates privilege escalation with PowerUp and Invoke-Mimikatz with PowerSploit. All of this happens without leaving Beacon:
A lot of care went into designing this feature for its post-exploitation use case. Expressions run, in the background, for as long as necessary. Each time Beacon checks in, it will grab output from each PowerShell script that’s still running.
For the non-PowerShell developers reading this, welcome to a new world of post-exploitation. You’ll feel like a giddy kid in a candy store as you browse through Github and see the easy-to-use features available to you now.
PowerShell developers, there’s something here for you too. You no longer need to design post-exploitation capabilities that bundle their own communication and delivery methods. You can just load your favorite tools and use Beacon to drive them.
Covert VPN Revamp
While PowerShell integration is the headline feature, Cobalt Strike 2.1 has a lot of other goodies. The Covert VPN feature had a good deal of maintenance. The VPN client is now a Reflective DLL which makes deployment much smoother. Covert VPN also gained a TCP (Bind) data channel to tunnel frames through meterpreter.
HTML Application Attack
Cobalt Strike 2.1 also gains the HTML Application User-driven attack. I don’t think this is going to change anyone’s life, but you can never have too many options to get a foothold in a target network. This package generates an HTML Application that drops and runs an executable. I opted to tie this attack to an executable as this gives you flexibility to drop a silent executable, a document dropper executable, or something else.
Malleable SSL
This release also builds on the Malleable C2 feature added in Cobalt Strike 2.0. You may now specify values for the self-signed SSL certificate Beacon’s web server uses. This is an opportunity to introduce indicators that mimic SSL-enabled remote access tools.
There’s a lot more in this release. You’ll want to consult the Release Notes for the full picture. Licensed users may use the built-in update program to get the latest.