Currently, I’m debating a class of social engineering “packages” to force SMB requests against an attacker controlled system. Ideas include packages to generate LNK files, host a WPAD server, etc.
This created a bit of an identity crisis though. I see Cobalt Strike as a tool for a penetration tester to emulate the capabilities of a motivated external actor. Sadly, many awesome SMB attacks require a physical presence on the target’s network.
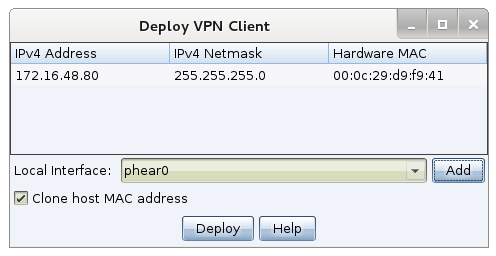
To put this issue to rest, I decided to build a feature to allow a motivated external attacker the ability to work as-if they are physically present on the target’s network. This feature is Covert VPN.
Covert VPN is a layer 2 pivoting capability for Cobalt Strike. It creates a network interface on your system that is bridged into the target’s network through a channel of your choosing. Covert VPN can tunnel its traffic over UDP, TCP, or HTTP channels
Once an interface is active, you can sniff packets, start rogue services, use external scanners and attack tools–pretty much whatever you want.
Covert VPN is in the latest version of Cobalt Strike.